HOW WE HELP
vPenTest
Automated Network Penetration Testing


Network Penetration Testing with vPenTest: Affordable, Accurate, and On-Demand
Introducing vPenTest, a full-scale penetration testing platform that incorporates the latest knowledge, methodologies, techniques, and commonly used tools of multiple consultants into a single platform. vPenTest is designed to make network penetration testing more affordable, accurate, faster, consistent, and not prone to human error. Our proprietary framework continuously grows based on our research and development, enabling us to modernize the way penetration tests are conducted.
vPenTest Solves Today's CHALLENGES
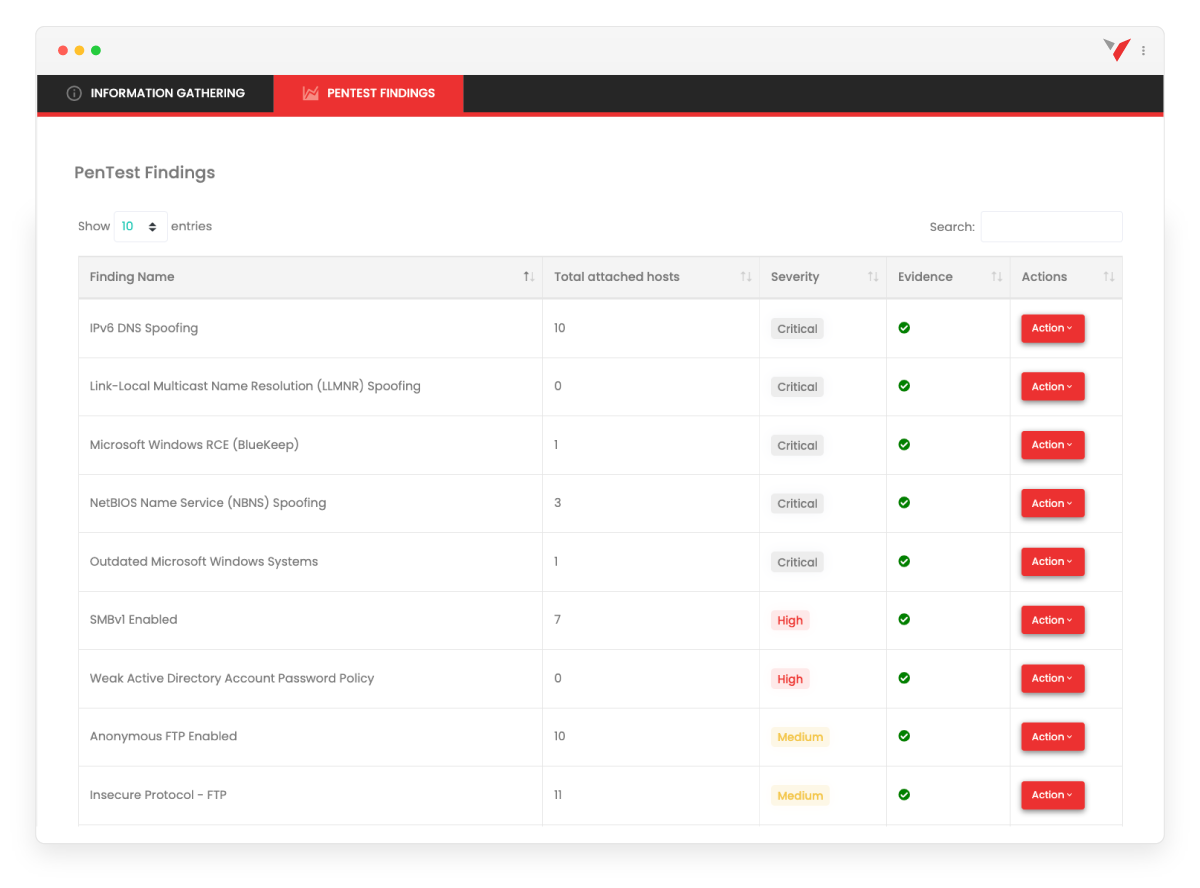
Traditional methods of seeking a qualified vendor for network penetration testing can be time-consuming and challenging. However, with vPenTest, we solve all of these challenges. Our platform provides quality deliverables that effectively communicate what vulnerabilities were identified, what risk it presents to the organization, as well as how to remediate those vulnerabilities from a technical and strategic standpoint.
Companies face some of the following challenges when looking for a qualified vendor:
- Seeking a vendor that is available to perform the penetration test.
- Interviewing the consultants to ensure their experience is advanced.
- Hoping communication is consistent and frequent to ensure knowledge transfers between consultants and the primary point of contact.
- Ensuring the vendor doesn’t sell a vulnerability assessment as a penetration test.
- Quality deliverables that effectively communicate what vulnerabilities were identified, what risk it presents to the organization, as well as how to remediate those vulnerabilities from a technical and strategic standpoint. The list goes on!
ON-DEMAND RISK MANAGEMENT
COMPLIANCE READINESS
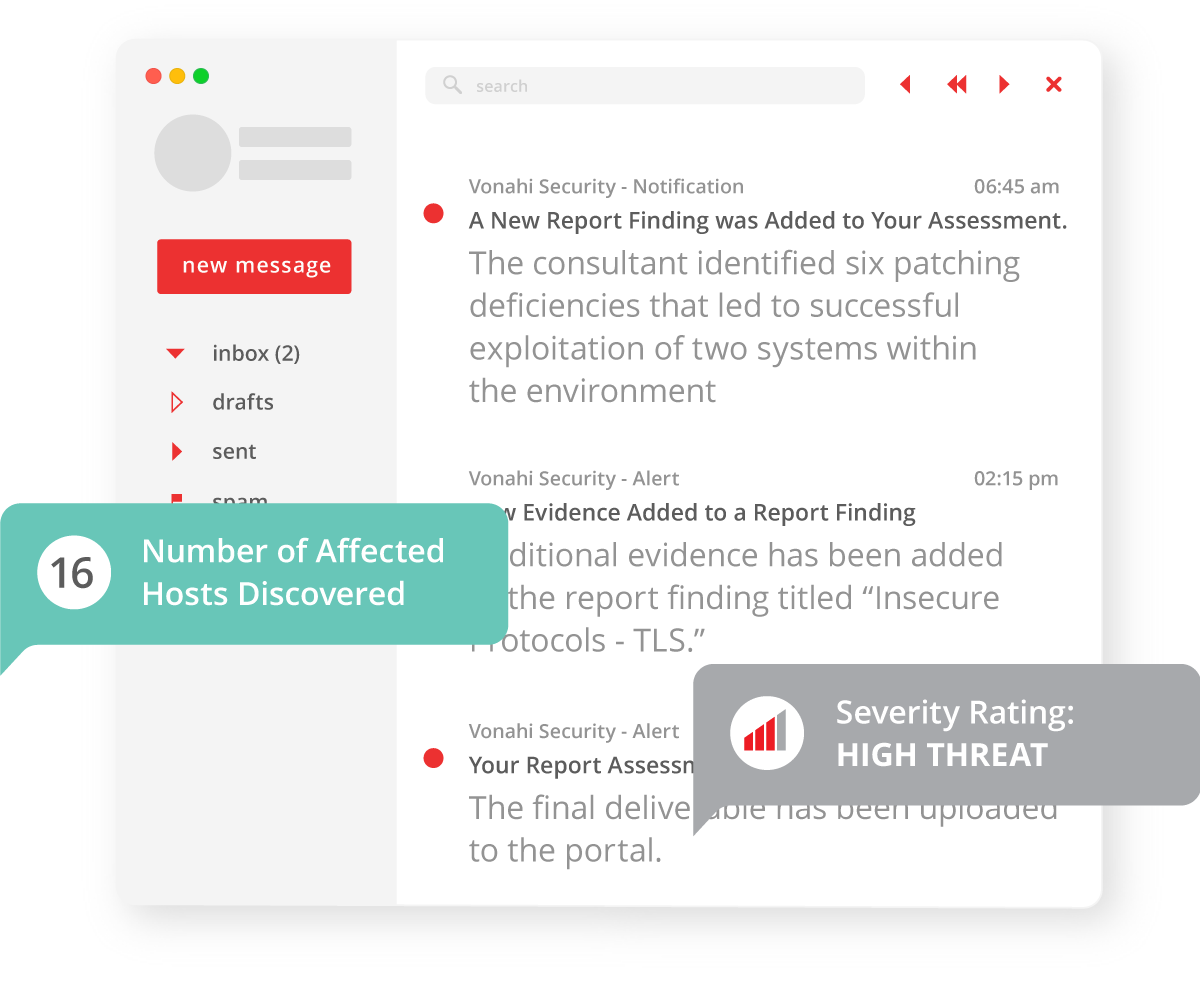
With vPenTest, meet compliance requirements with more scheduling flexibility and real-time alerts. We provide more flexibility in schedule, alerting, real-time activity tracking, as well as segmentation testing to confirm isolation of sensitive networks. In addition to ensuring compliance readiness, vPenTest also tests for security deficiencies that deviate from security best practices.
ALWAYS BE IN THE KNOW
Our progress tracker ensure that your IT team knows exactly what the progress is of the engagement, when it’s expected to be completed, as well as any preliminary findings that we’ve identified. Your team will always know when and what activities are taking place.
VALIDATE YOUR SECURITY CONTROLS
To maximize the value of our penetration tests, vPenTest includes an activity log that monitors all activities performed during the penetration test. Network teams can correlate our activities with their SIEM and incident response procedures. Every engagement is essentially a purple team assessment.
PRE- AND POST-BREACH SIMULATION
Host Discovery - Performing discovery of systems and services within the environment targeted, and including active systems and port scanning.
Enumeration - Enumeration of services and systems to identify potentially valuable information, including vulnerability analysis..
Post-Exploitation - After gaining an initial foothold on a system, vPenTest automatically attempts to launch privilege escalation attacks. New attack avenues will also be analyzed to determine if more access into the environment or sensitive data could be established.
Backed by Experience
Our platform vPenTest, is backed by consultants with over 10 years of experience, holding certifications ranging from CISSP, eCPPT, OSCP, OSCE, CEH, and more. We have conducted hundreds of security assessments for hundreds of clients within various industries, and we’ve taken the most valuable strengths and combined them into a platform that allows our customers to have high quality assessments performed at their own convenience.