Identify your Risks in Real-time with
Automated Network Penetration Testing
Deploy. Click. Go.
Hello World, Meet
The industry’s most valued automated network penetration testing platform.
- Complete flexibility to schedule an internal or external network penetration test anytime you need it.
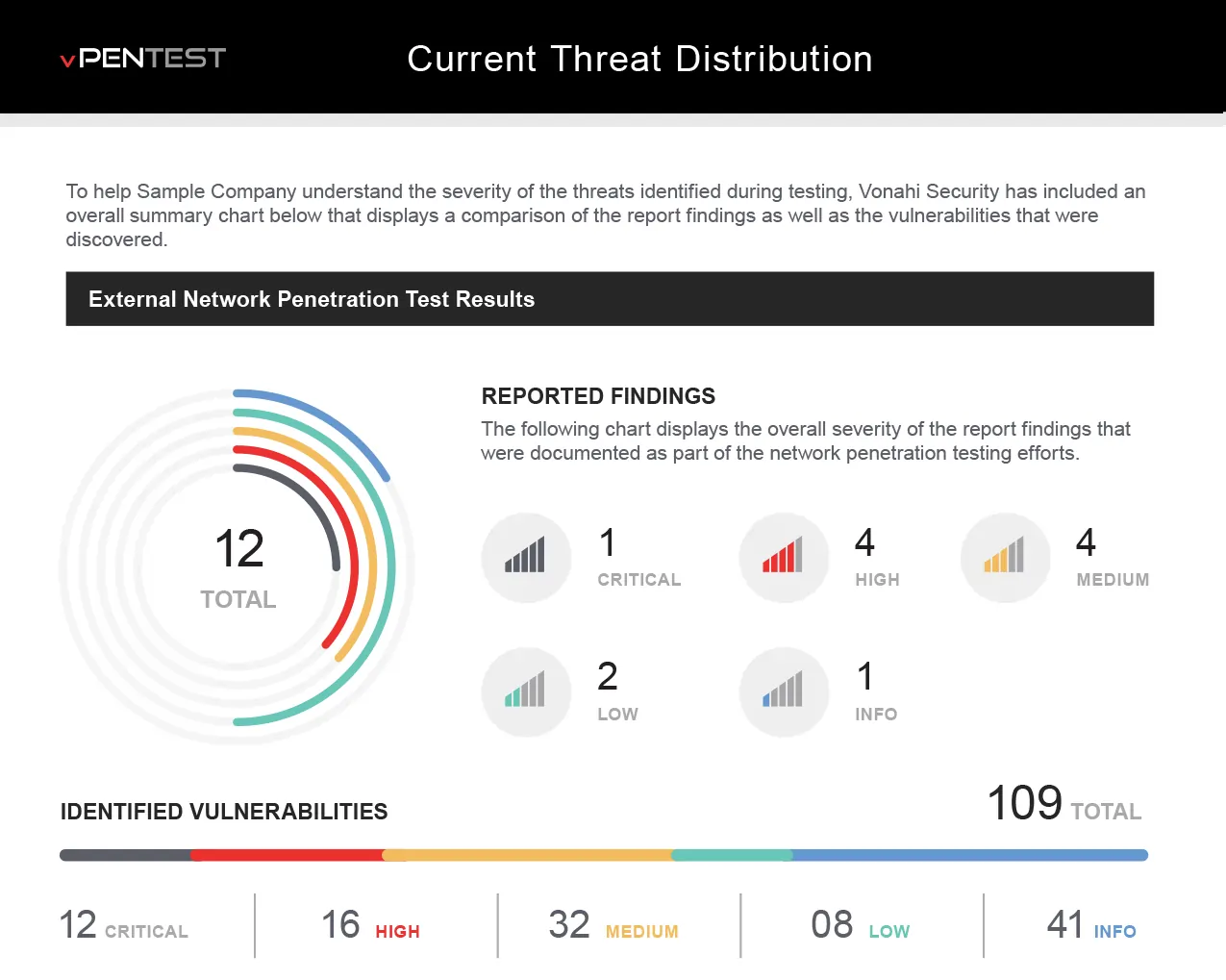
- More extensive and goes way beyond an automated vulnerability scan.
- Over 60% less than the cost of a traditional or manual network penetration test.
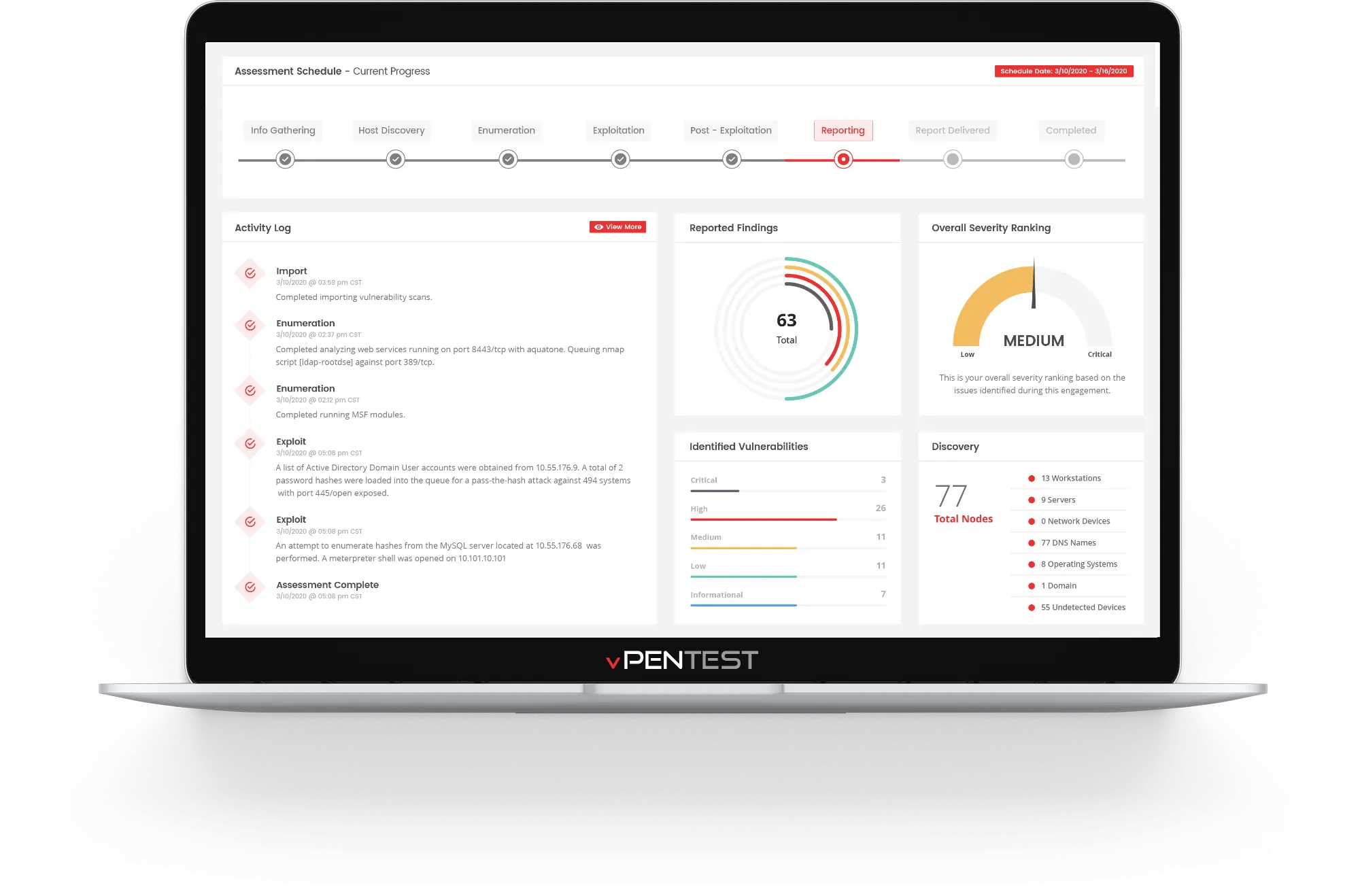
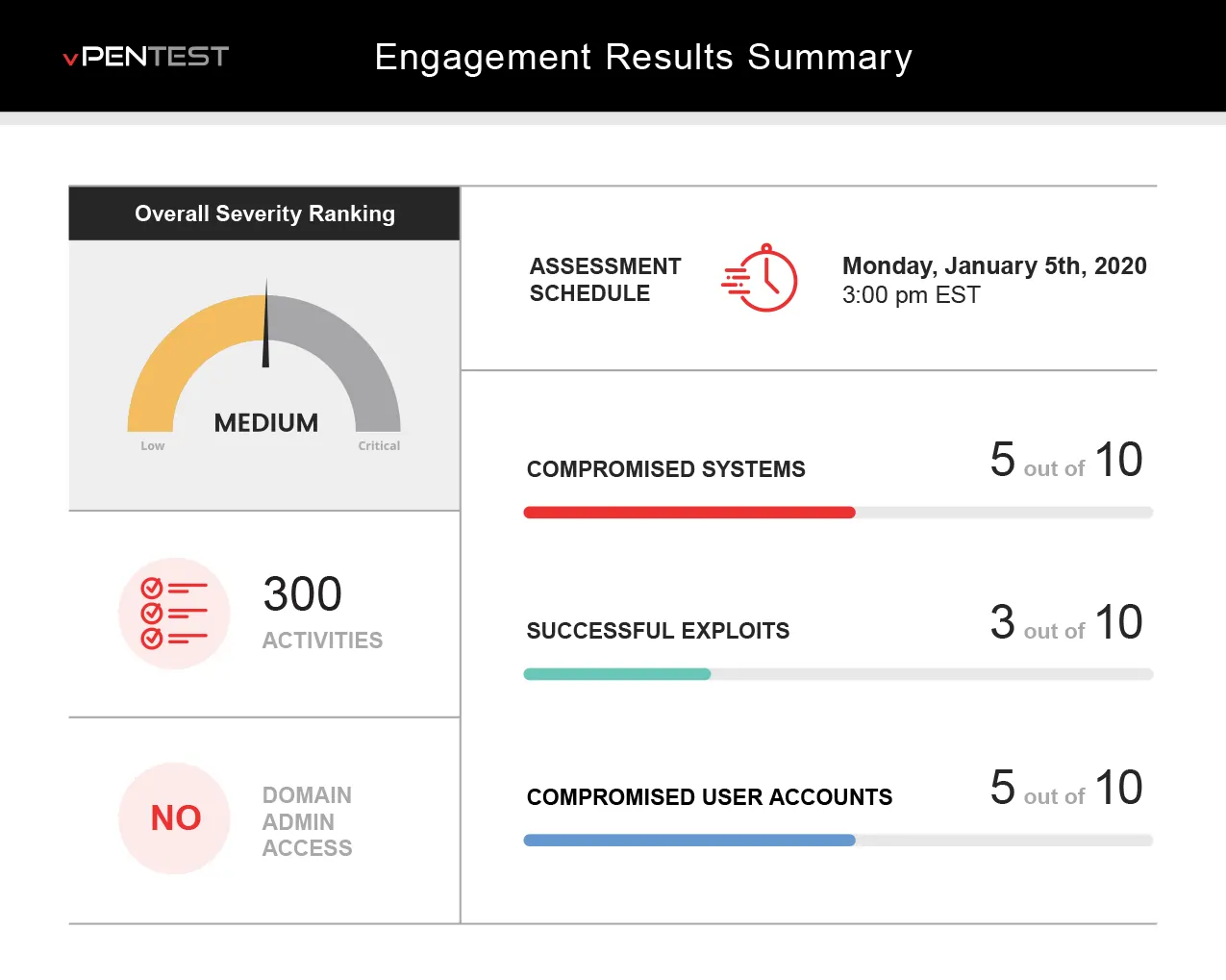
- Real-time monitoring of network penetration test and progress.
- The entire solution meets compliance requirements for regulated industries: PCI, HIPAA, SOC2, etc., and cyber insurance.
- Backed by OSCP and OSCE certified consultants with 10+ years experience.
Test Your Defenses
Our Modern Approach to PenTesting
Continuous
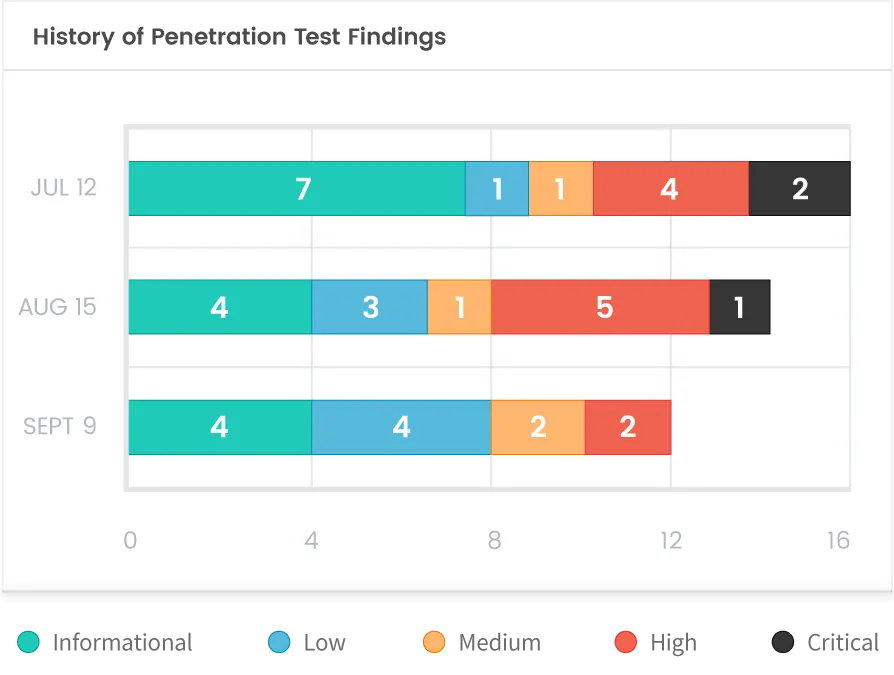
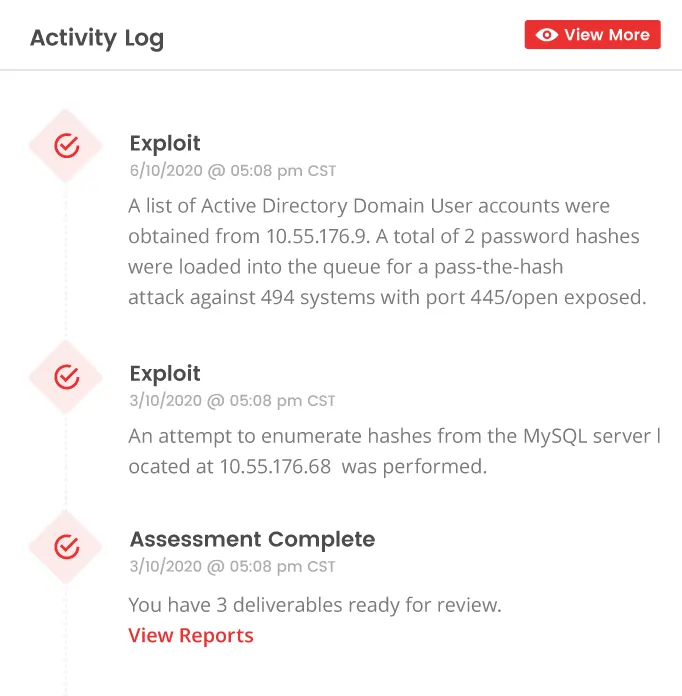
Real-time Visibility
Save Time & Be in Control
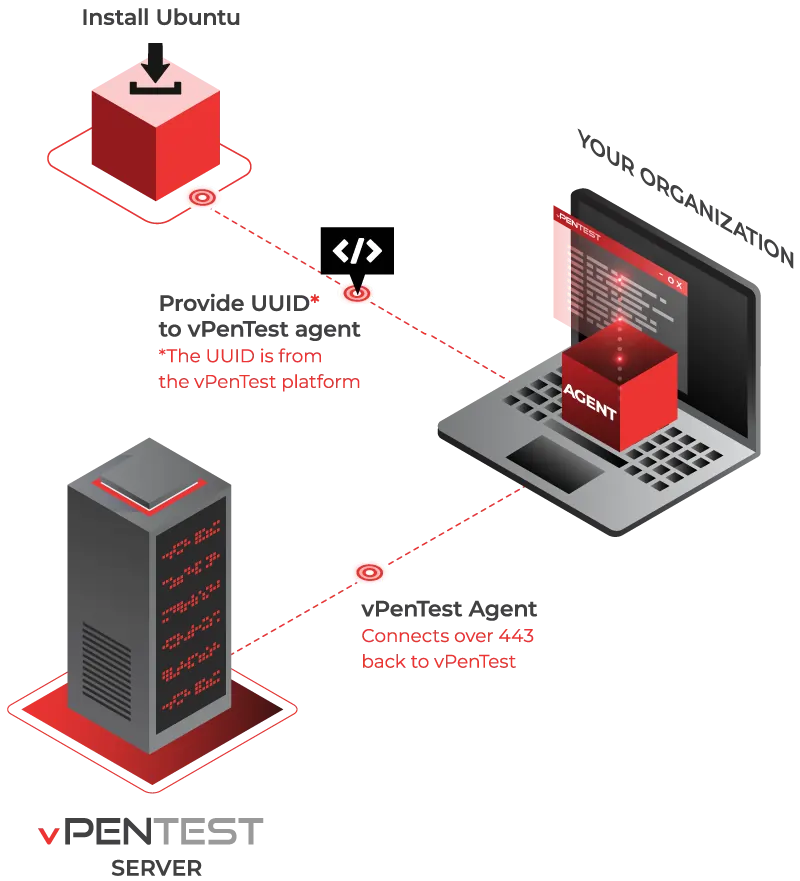
Red Team on Demand
Quality Reports to Share With the Team
A Few Bytes From Our Partners
OUR LATEST FEATURES

Dark Web ID Integration
Use compromised credentials from the dark web during network pentests to reveal the impact of stolen passwords, validate security controls like 2FA, and strengthen defenses with deeper insights and stronger security outcomes.
vPenTest API
Easily access your vPenTest data with simple API endpoints that connect to your systems, pull key data like organizations, schedules, and reports, and streamline your security operations.

Automated Executive PowerPoint Presentations
Automatically generate executive-ready presentations with AI-driven speaker notes that highlight your top 3 security risks, translate them into business terms, and help prioritize high-impact remediation.

AI-Enhanced Executive Summary Reports
Executive summaries now include AI-powered insights that translate technical findings into clear, business-focused language. Get the scope, key findings, impact, and prioritized remediation steps.

EMEA Data Region
vPenTest customers in Europe, the Middle East, and Africa can now store data from our EMEA data region. This improves performance, and helps meet GDPR and other compliance requirements.